8 minutes
SOAR EDR Cloud Project (LimaCharlie and Tines)
Integration of SOAR and EDR featuring LimaCharlie and Tines. Learning how to automate security workflows, and enhancing cybersecurity posture effectively.
For VMs, I will be using Vultr cloud resources again. I have spun a windows 10 machine with firewalls configured to RDP only from my public IP.
Project Main Takeaways:
Creating custom detection & response rule in LimaCharlie
Creating a playbook that integrates Slack, Tines, Email.
Playbook contents:
1. Send a Slack message
2. Send an Email (containing info about the detection)
3. Generate a user prompt (asking analyst to isolate machine yes/no)
4. If Yes, then Isolate.
Part 1 Objective :
- Setting up LimaCharlie on my laptop.
- Connecting my cloud windows VM to LimaCharlie.
Created an account on LimaCharlie and followed the required steps. LimaCharlie gives us a basic guide after we create an account.
Under Sensors in limaCharlie, I went to Installation Keys and created a new key.
This key will be needed in order to install the endpoint sensor onto my Windows VM.
On the same page, under Sensor Downloads, I copied the Windows64 bit download link and pasted onto my VM and to install it, I followed the DOCS.
To confirm it is installed , I checked the sensors page and there it was:
We can click it to view additional details.

We can view various information on the left side to find evil.
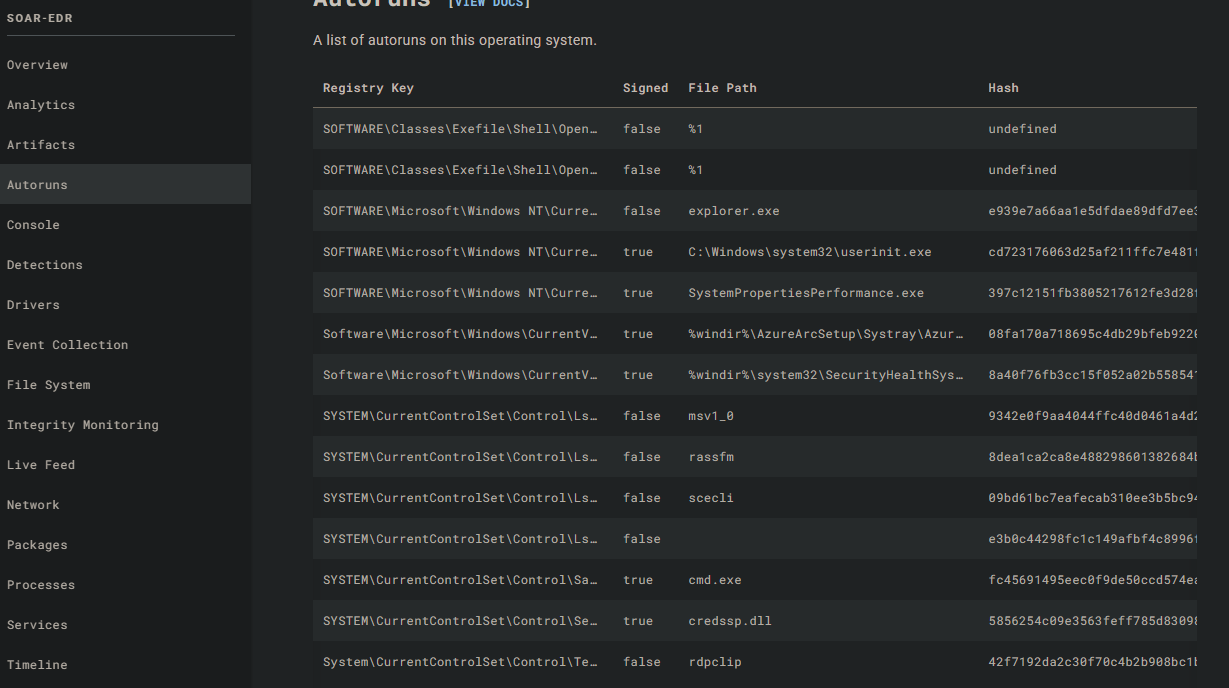
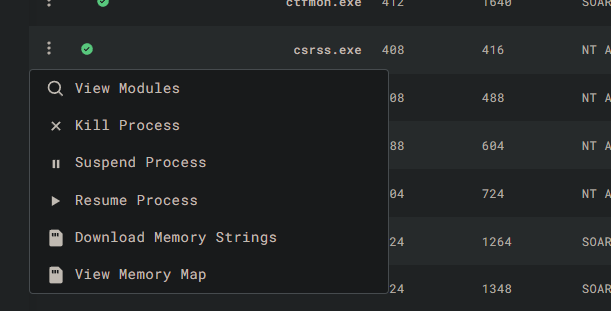
For example, to look for persistence , I can look at the autoruns section. I can also run remote commands from the console section. I can even kill processes:
Part 2 Objective :
- Generating Telemetry with Lazagne (a password recovery tool).
- Creating detection and response rules.
I downloaded Lazagne and ran it using powershell.
It also got picked up in LimaCharlie , under the Timeline section , we can see the detection.
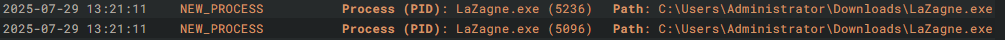
To get further info on that file , we can click on the New_Process event and it will show file hashes, username, parent process id and many more which can aid us in the investigation process.
Now to create detection and rules, I went to D&R Rules under Automation section.
There we can add a new rule.
This is for detecting lazagne:
events:
- NEW_PROCESS
- EXISTING_PROCESS
op: and
rules:
- op: is windows
- op: or
rules:
- case sensitive: false
op: ends with
path: event/FILE_PATH
value: LaZagne.exe
- case sensitive: false
op: contains
path: event/COMMAND_LINE
value: LaZagne
- case sensitive: false
op: ends with
path: event/COMMAND_LINE
value: all
- case sensitive: false
op: is
path: event/HASH
value: '3cc5ee93a9ba1fc57389705283b760c8bd61f35e9398bbfa3210e2becf6d4b05'
This rule gets triggered when a new or existing process is detected and sets this condition which must be true:
- The OS is Windows
- At least one of the following is true:
- File path ends with
LaZagne.exe - Command line contains
LaZagne - Command line ends with
all - File hash matches:
3cc5ee93a9ba1fc57389705283b760c8bd61f35e9398bbfa3210e2becf6d4b05
- File path ends with
If detected, this will be the response:
- action: report
metadata:
author: ChaoNeil
description: TEST - Detects Lazagne Usage
falsepositive:
- Unlikely
level: medium
tags:
- attack.credential_access
name: Hacktool Lazagne SOAR-EDR
Under the Advanced tab of the D&R Rules , I can test this rule to see if it works, just have to paste in the process event data from Timeline section.
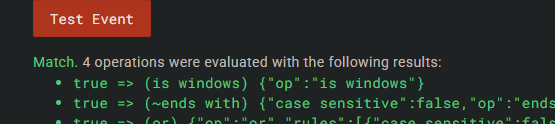
It works! Also I ran lazagne.exe on my VM to generate this detection alert and looking at the Detections section , I can see an alert pop up:
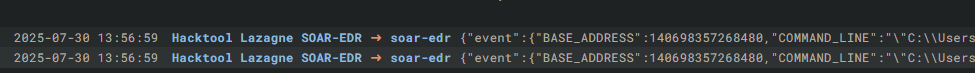
It shows the name value as message in the response. I can simply click the alert, and it will show me detailed information.
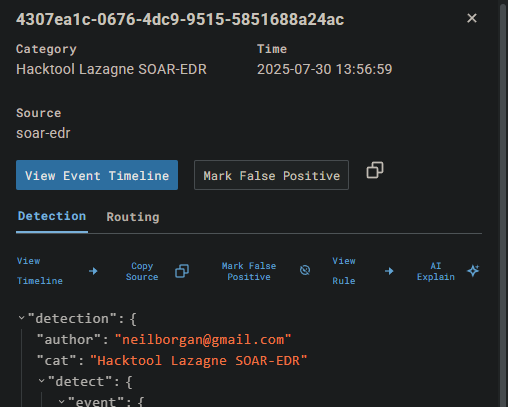
Part 3 Objective :
- Setup Slack and Tines
- Test connection (LimaCharlie + Tines) to make sure our SOAR is seeing the detection generated by LimaCharlie.
Tines is a tool that helps security and IT teams automate their work using AI.
After signing up for Tines, I found the UI and workflow process comparable to Shuffle’s, maybe because both are SOAR (Security Orchestration, Automation, and Response) platforms designed to automate security workflows. So I found the process/workflow of integrating tines with LimaCharlie very similar.
I took a webhook block in Tines and named it Retrieve Detections and copied the webhook URL to LimaCharlie’s output section. Outputs allows us to integrate data from LimaCharlie into other cloud tools. In the Output’s section there are 4 sub-sections that I need to specify (Stream, Destination, Configure, Sample). Following this process, I pasted the webhook url in the configure tab and saved the output.
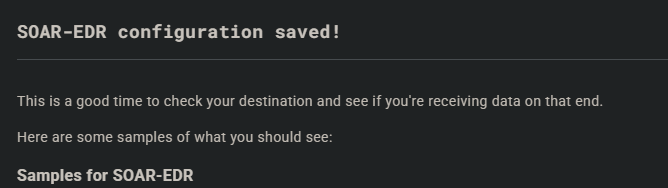
To generate sample, I reran lazagne on my cloud VM to generate alerts and to check if it was working as intended.
Testing connections:
When I checked back at Tines, I saw alerts being transmitted from over LimaCharlie. Working good so far.
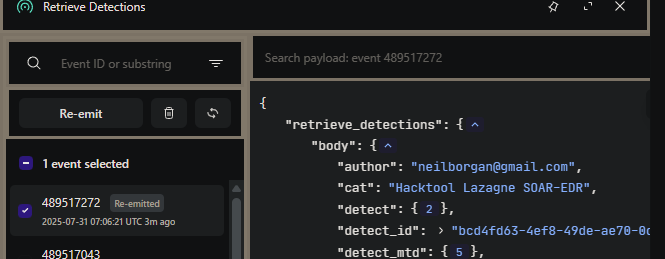
The link between LimaCharlie and Tines has been established.
Part 4 Objective :
- Create Playbook
- Playbook contents:
- Send a Slack message
- Send an Email (containing info about the detection)
- Generate a user prompt (asking analyst to isolate machine yes/no)
- If Yes, then Isolate.
The alerts that I received in Tines now should also generate a message in Slack stating the above prompt. Now to do that, I added Tines app in slack via slack automations and followed the required steps.
After doing these steps I was able to link and establish connections between slack and tines.
Setting up the workflow parameters in tines to send message to slack is similar to Shuffle, I had to copy channel ID of slack, type in the message that I want to convey etc. This is the output:
Now that I have confirmed that it can send messages, its time to send a message with details. I will use this format:
- Title
- Time
- Computer Name
- Source IP
- Process
- Command Line
- File Path
- Sensor ID
- Link to the detection (if applicable)
I will find these values to their respective field names that are similar to LimaCharlie’s detection alerts. Eg: the Computer Name is referred as hostname. All can be found in under events in the retrieve detection webhook that i created earlier.
Title: <<retrieve_detections.body.cat>>
Time: <<retrieve_detections.body.detect.routing.event_time>>
Computer Name: <<retrieve_detections.body.detect.routing.hostname>>
Source IP: <<retrieve_detections.body.detect.routing.int_ip>>
Username: <<retrieve_detections.body.detect.event.USER_NAME>>
Process: <<retrieve_detections.body.detect.event.FILE_PATH>>
Command Line: <<retrieve_detections.body.detect.event.COMMAND_LINE>>
Sensor ID: <<retrieve_detections.body.detect.routing.sid>>
Detection Link: <<retrieve_detections.body.link>>
This is the complete message format that I used to send message in slack. I pasted this in slack message field in tines.
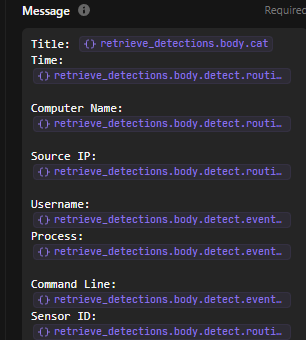
And this is message that I got in Slack after testing run:
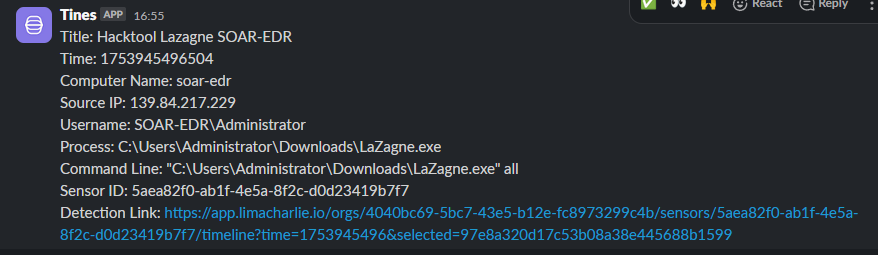
Pretty cool huh!
I also implemented this in an email setting. I had to edit out the email body field in order to render it nicely.
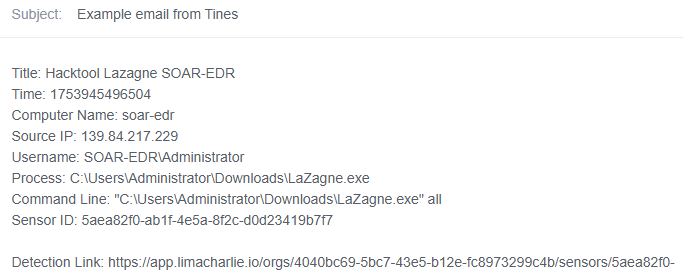
–
Adding Prompt (NO):
I have to now add a prompt asking to isolate the affected machine. I grabbed a send email block in tines and made a simple page with boolean (yes/no). In the page edit section, I copy-pasted my previous message format and it worked.
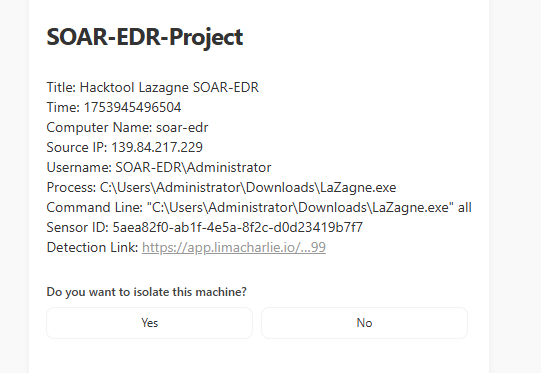
If the user selects No, It should send a message to Slack.
To achieve that I pulled a Trigger block and configured it. Under Rules, I selected the user prompt and set it to false, since this is what will “trigger” if it is selected “No”.
Then I took another slack message block and edited it to include a message that will tell us what to do next if the condition is “False”.
To test this whole workflow, I ran it from the start (webhook), got texts on my slack channel as well as my email, selected “No” and this was the resulting text that I received:
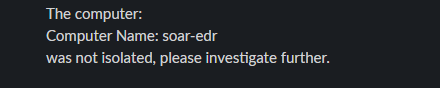
Adding Prompt (YES):
Time to do the same but now for the “Yes” prompt which will isolate that machine from LimaCharlie. I grabbed another trigger block , renamed it to “Yes” and grabbed a LimaCharlie block from the templates. The template already had a “isolate Sensor” by default so I just edited that a little.
Under the Url tab of that block, I specified the “sid” (sensor id) field value from the previous message format message.
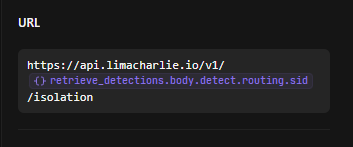
However to send the isolation signal to LimaCharlie, I need to link the API key to Tines.
From the tines’s credentials section, I made a LimaCharlie API Key variable and saved it. I grabbed the key from LimaCharlie --> Access Management --> REST API --> Org JWT api key.
Then on my workflow page in Tines, under Credentials, I selected my newly created “API KEY” variable and linked it.

Then I re-ran the entire process and alas, the machine is now finally isolated. I confirmed it by going to the Overview section of my sensor in LimaCharlie.
The VM will lose internet access unless it rejoins network.
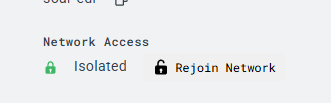
I also added some text that will notify me in Slack if the machine is isolated. There is already a LimaCharlie template for that, just needed to edit the sid and link to limacharlie API.
This is my workflow in the end:
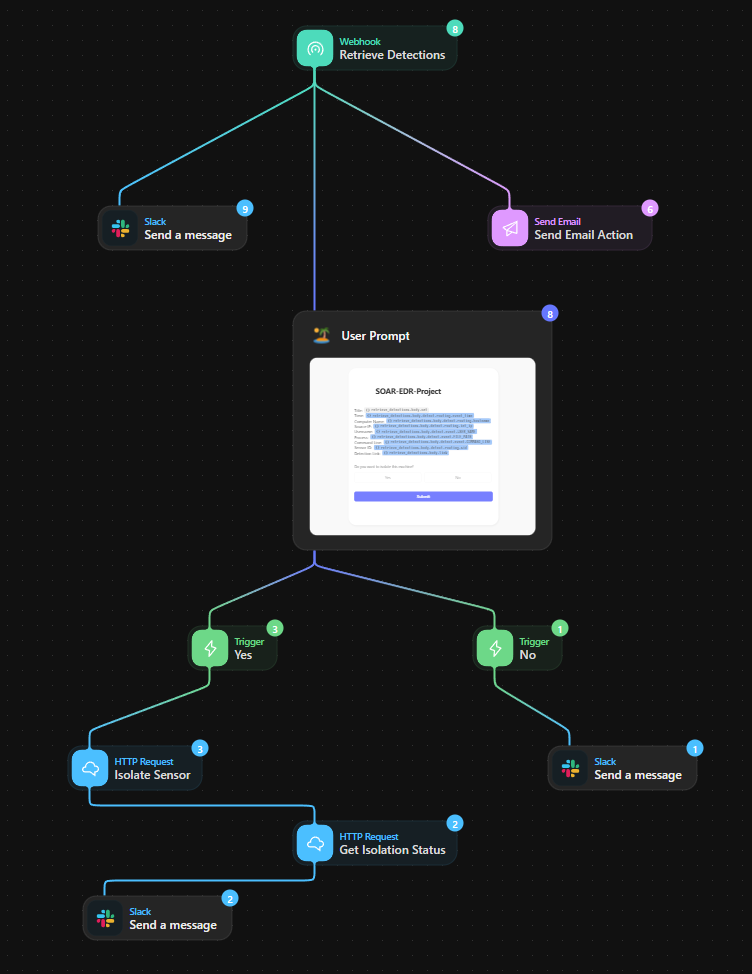
Conclusion
This was my second SOC project and I must say I got pretty overwhelmed in the end. Even after following guides , I encountered many errors and got frustrated but eventually solved it.
This project gave me hands-on experience integrating SOAR (Tines) and EDR (LimaCharlie) tools to automate security workflows. I learned how to create detection rules, trigger alerts, and build end-to-end response playbooks that involve Slack notifications, email prompts, and live host isolation. This process deepened my understanding of modern SOC operations and how orchestration platforms can significantly improve incident response efficiency.
1557 Words
0000-12-31 16:07